Post by : Anees Nasser
Every day, billions of people send personal messages without a second thought. Conversations about health, money, relationships, work, and private life all flow through glowing screens. Apps promise safety with technical words that sound reassuring. One phrase appears more often than any other: “end-to-end encryption.”
It sounds powerful. It feels comforting. But what most users do not realize is that encryption is not the same as total security. It is not a cloak of invisibility. It is not a legal shield. It is not an invincible wall that nothing can penetrate.
End-to-end encryption is a tool. A strong one — but limited.
Understanding what this term really means is essential in an age where privacy is as valuable as money. Because while encryption protects messages in transit, it does not always protect you.
Let’s break down what end-to-end encryption does, what it doesn’t, and why many people misunderstand its true power.
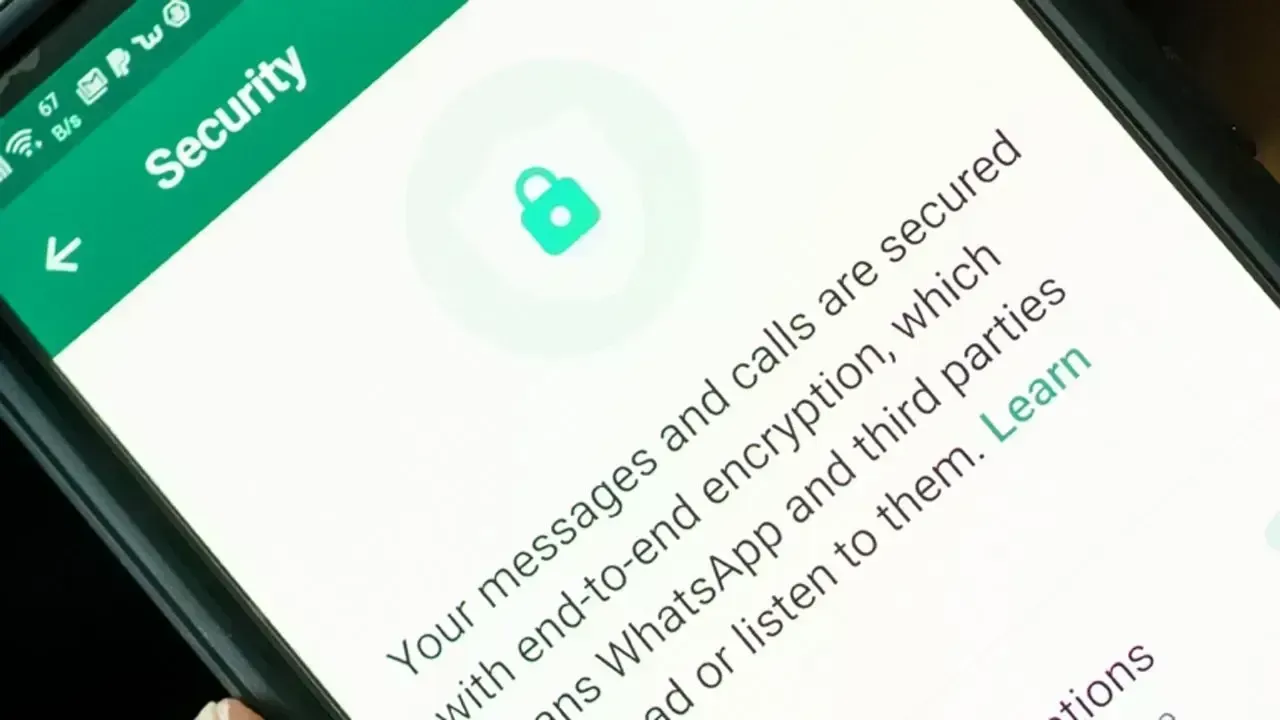
End-to-end encryption means that your message is converted into unreadable code before it leaves your phone and stays unreadable until it reaches the intended recipient’s device.
Only the sender and the receiver can read the message.
Not the app.
Not the company.
Not hackers.
Not internet providers.
In theory.
Imagine putting a letter inside a safe, locking it, and sending it by courier. The courier carries the box but cannot open it. Only the person with the correct key at the other end can unlock it.
That is the simple idea behind encryption.
When you send a message, several invisible operations take place in the background:
Your message is mathematically scrambled using a key. Without that key, the message looks like random data.
The scrambled message travels across networks and servers in unreadable form.
The receiver’s device uses a digital key to convert that scrambled message back into text.
At no point during transmission can anyone intercept and read it as plain text.
That is the promise.
Many popular apps claim end-to-end protection, including platforms like WhatsApp, Signal, and device-level features found in products from Apple and Google.
Each platform implements encryption differently. Some protect chats by default. Others offer optional encrypted conversations.
Encryption is not a single switch — it is a spectrum.
Encryption is very good at specific things.
Your messages cannot be read by hackers spying on Wi-Fi networks.
Internet providers cannot scan message contents.
Apps themselves cannot read message text in encrypted chats.
Mass data leaks from servers do not expose message content directly.
This makes encryption essential in protecting speech and privacy.
This is where misunderstanding begins.
Encryption protects your message in transit.
It does not protect:
• Someone physically unlocking your phone
• Malware installed on your device
• Spyware that captures your screen
• Apps with rogue permissions
• Keyloggers or screenshot tools
If your phone is compromised, encryption becomes irrelevant.
Because messages are readable on your screen.
Many users back up chat history to cloud accounts.
This is where encryption often breaks down.
If your chats are stored unencrypted in cloud storage, authorities or hackers can access backups even if they cannot read live messages.
End-to-end encryption does not automatically apply to backups unless clearly stated.
Encryption protects content, not context.
Information such as:
• Who you message
• When you message
• How often you message
• Where you are
• Which device you use
This data is recorded.
Metadata can reveal your habits even without reading messages.
In intelligence analysis, metadata is often more powerful than content.
Anyone can screenshot a message.
Encryption does not stop forwarding.
It does not erase evidence.
If the recipient saves or shares, privacy evaporates instantly.
No encryption system operates independently of human behaviour.
A perfectly encrypted app is useless if:
• Users fall for scams
• Partners misuse access
• Friends betray trust
• Accounts are hijacked
• Passwords are reused
• Devices are shared carelessly
Security fails where behaviour ignores risk.
Governments often criticise encryption.
Why?
Because encrypted messages block surveillance.
Authorities argue that criminals hide behind private platforms.
Privacy advocates argue encryption protects ordinary citizens.
Both arguments exist simultaneously.
Encryption is neutral.
Usage isn’t.
Directly? Rarely.
Indirectly? Often.
They may:
• Request backups
• Target devices, not servers
• Access account data
• Monitor metadata
• Use spyware
• Obtain login credentials
Encryption is strongest on paper.
In practice, people are targeted — not algorithms.
Trust sells.
Encryption has become:
• A marketing badge
• A competitive advantage
• A privacy statement
• A reputation shield
More privacy claims mean more users.
But no company controls how users behave afterwards.
Security language is comforting.
But absolute safety doesn’t exist online.
Encryption makes breach harder.
Not impossible.
Just slower.
No.
Some apps:
• Encrypt everything
• Refuse to store messages
• Minimize metadata
Others:
• Store logs
• Back up data
• Share information with partners
• Retain transaction history
“Encrypted” does not equal “private”.
Always check what else is collected.
Reality: Anyone with access to your device can.
Reality: Metadata still tells stories.
Reality: Security does not replace judgment.
Reality: They defeat encryption entirely.
Reality: It never has.
Encryption is one layer — not the system.
Biometric security is your first defense.
Account theft defeats encryption.
Many apps track beyond reason.
Cloud settings often ignore security by default.
Encryption is strong — but side channels exist.
Digital memory never forgets.
Some apps offer self-destructing messages.
This does not guarantee deletion.
Receivers can:
• Record screens
• Use second devices
• Store images
• Export chats
“Disappearing” often means disappearing publicly, not privately.
For:
• Journalists
• Activists
• Whistleblowers
• Political dissidents
• Domestic violence victims
• Corporate investigators
• Privacy advocates
It can be life-saving.
For casual chats, it protects dignity.
Many parents assume encryption protects kids.
But encryption hides activity — it doesn’t guarantee safety.
Children need:
• Education
• Supervision
• Open conversation
• Digital awareness
Privacy without literacy breeds danger.
It protects data.
Not decisions.
It secures transport.
Not relationships.
It hides content.
Not consequences.
Encryption will grow stronger.
But surveillance tools will evolve too.
This is not a war someone ‘wins’.
It is a permanent arms race.
Privacy will always exist on borrowed time.
End-to-end encryption is a powerful invention.
It protects speech in an age of surveillance.
It gives freedom in restrictive systems.
It offers dignity in digital life.
But it is not magic.
It doesn’t cancel recklessness.
It doesn’t stop screenshots.
It doesn’t protect emotions.
It doesn’t defend against bad decisions.
Encryption secures messages.
Wisdom secures lives.
And in the digital world —
Wisdom is the strongest password you will ever create.
This article is provided for informational purposes only and does not constitute legal, cybersecurity or technical advice. Readers should consult qualified professionals for personal data protection strategies.










Kazakhstan Boosts Oil Supply as US Winter Storm Disrupts Production
Oil prices inch down as Kazakhstan's oilfield ramps up production, countered by severe disruptions f

Return of Officer's Remains in Gaza May Open Rafah Crossing
Israel confirms Ran Gvili's remains identification, paving the way for the Rafah border crossing's p

Border 2 Achieves ₹250 Crore Globally in Just 4 Days: Sunny Deol Shines
Sunny Deol's Border 2 crosses ₹250 crore in 4 days, marking a significant breakthrough in global box
Delay in Jana Nayagan Release as Madras HC Bars Censorship Clearance
The Madras High Court halts the approval of Jana Nayagan's censor certificate, postponing its releas

Tragedy Strikes as MV Trisha Kerstin 3 Accident Leaves 316 Rescued
The MV Trisha Kerstin 3 met an unfortunate fate near Jolo, with 316 passengers rescued. The governme

Aryna Sabalenka Advances to Semi-Finals, Targeting Another Grand Slam Title
Top seed Aryna Sabalenka triumphed over Jovic and now faces Gauff or Svitolina in the semi-finals as